Assessing Vulnerabilities and Risks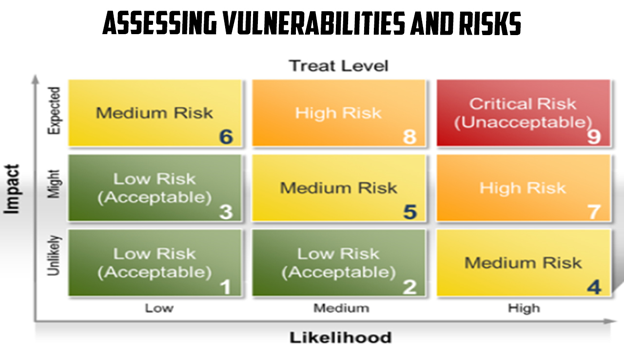
When it comes to safeguarding operational technologies in critical infrastructure, a crucial initial step is assessing vulnerabilities and risks. This process involves a comprehensive evaluation of the systems to identify weak points and potential entry points for cyberattacks. By conducting a thorough analysis, organizations can gain valuable insights into the potential threats and vulnerabilities that could compromise their operational technologies. This assessment helps prioritize the implementation of appropriate security measures and allocate resources effectively. Mapping the dependencies and interconnectedness of operational technologies within critical infrastructure further enhances the understanding of potential cascading effects. By conducting a robust assessment of vulnerabilities and risks, organizations can lay a solid foundation for developing a proactive and effective cybersecurity strategy.
Assessing vulnerabilities and risks in critical infrastructure requires a systematic and meticulous approach. With an increasing number of sophisticated cyber threats, it is imperative to stay ahead by identifying potential weaknesses before they are exploited. By establishing a comprehensive security framework, organizations can create guidelines and protocols that ensure consistent and effective security measures across all operational technologies. Access control mechanisms and authentication protocols play a crucial role in preventing unauthorized access to critical systems. Additionally, developing an incident response plan is essential to effectively mitigate the impact of cyber incidents. By assessing vulnerabilities and risks, organizations can take proactive steps towards safeguarding their operational technologies, enhancing their resilience against potential cyber threats.
Establishing Robust Security Policies and Procedures
Establishing robust security policies and procedures is paramount when it comes to safeguarding operational technologies in critical infrastructure. A comprehensive security framework provides organizations with clear guidelines and protocols to ensure consistent and effective security measures across all systems. By developing and implementing these policies, organizations can establish a strong foundation for protecting their critical infrastructure from cyber threats. Access control and authentication mechanisms play a crucial role in preventing unauthorized access, while incident response planning enables a swift and coordinated response to mitigate the impact of potential cyber incidents. With a focus on establishing robust security policies and procedures, organizations can enhance their cybersecurity posture and minimize the risk of disruptions to their operational technologies.
In today’s ever-evolving threat landscape, it is essential for organizations to establish robust security policies and procedures for safeguarding their operational technologies in critical infrastructure. These policies serve as a blueprint for ensuring the consistent implementation of security measures across all systems. By adhering to established protocols, organizations can effectively manage access control and authentication, preventing unauthorized individuals from compromising critical systems. Incident response planning is another vital aspect of robust security policies, enabling organizations to respond swiftly and effectively to cyber incidents, minimizing potential damages. By prioritizing the establishment of comprehensive security policies and procedures, organizations can strengthen their defenses, protect their operational technologies, and maintain the continuity of critical infrastructure operations.
Implementing Advanced Threat Detection and Prevention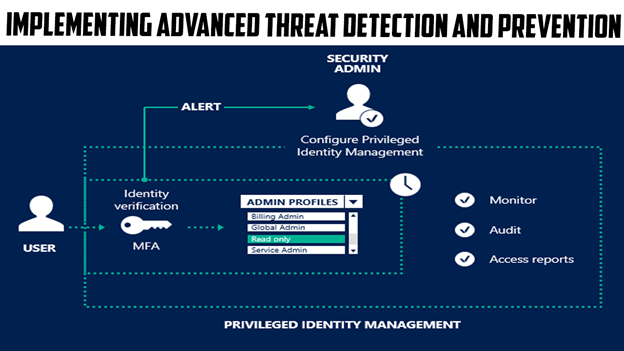
Implementing advanced threat detection and prevention measures is crucial in safeguarding operational technologies within critical infrastructure. With the evolving landscape of cyber threats, organizations need to stay ahead by deploying cutting-edge technologies and strategies. Intrusion detection systems play a pivotal role in monitoring network traffic and identifying potential threats in real-time. By analyzing patterns and anomalies, these systems can detect and alert security teams to potential cyberattacks, allowing for immediate response and mitigation. Integrating threat intelligence feeds and information sharing platforms further enhances the organization’s ability to stay updated on the latest threats and attack techniques. Coupled with robust endpoint protection measures, ‘’Dubai E-commerce” advanced threat detection and prevention mechanisms provide organizations with the means to proactively defend their operational technologies against malicious activities.
In the realm of critical infrastructure, implementing advanced threat detection and prevention measures is paramount to mitigate potential risks and secure operational technologies. Intrusion detection systems form a critical component of this strategy, continuously monitoring network traffic for suspicious behavior and indicators of compromise. By leveraging real-time threat intelligence, organizations can enhance their understanding of emerging threats and deploy proactive countermeasures. Additionally, robust endpoint protection solutions provide an added layer of defense by securing devices and preventing unauthorized access. By implementing a multi-layered approach to threat detection and prevention, organizations can detect and respond to cyber threats swiftly, minimizing the potential impact on their operational technologies. With advanced technologies and vigilant monitoring, organizations can fortify their critical infrastructure against evolving cyber threats.
Enhancing Network Segmentation and Isolation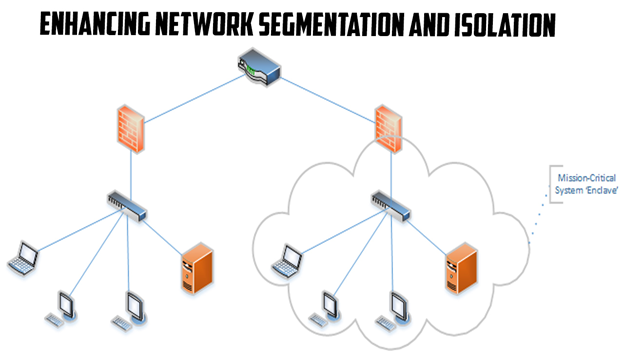
Enhancing network segmentation and isolation is a critical step in safeguarding operational technologies within critical infrastructure. By dividing the network into smaller, isolated segments, organizations can contain potential attacks and limit lateral movement in the event of a security breach. Network segmentation ensures that even if one segment is compromised, the rest of the network remains secure. Implementing a zero-trust architecture adds an extra layer of protection by requiring continuous authentication and authorization, even for internal network traffic. Furthermore, physically isolating critical systems from external networks through air-gapping provides an additional level of security. By enhancing network segmentation and isolation, organizations can effectively mitigate the risk of unauthorized access and protect their operational technologies from cyber threats.
In the context of critical infrastructure, enhancing network segmentation and isolation is paramount for ensuring the security of operational technologies. By dividing the network into smaller, isolated segments, organizations can create barriers that contain potential breaches and limit the spread of cyberattacks. This proactive measure prevents adversaries from gaining unauthorized access to critical systems and moving laterally within the network. Implementing a zero-trust architecture reinforces this security approach by requiring continuous authentication and authorization, regardless of the source or destination of network traffic. Additionally, air-gapping critical systems physically separates them from external networks, reducing the risk of remote attacks. By implementing robust network segmentation and isolation measures, organizations can significantly bolster the protection of their operational technologies and critical infrastructure, safeguarding against potential cyber threats.
Strengthening Resilience and Redundancy
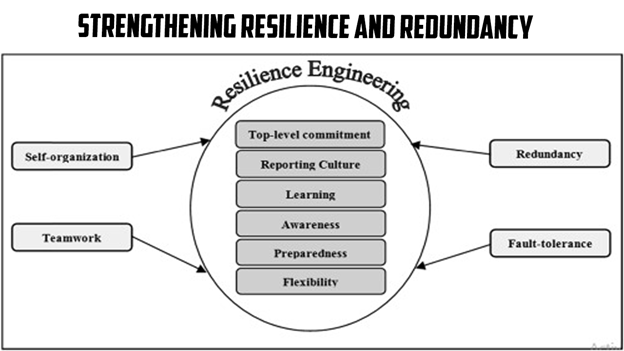
Strengthening resilience and redundancy is essential when it comes to safeguarding operational technologies within critical infrastructure. By implementing measures to enhance resilience, organizations can ensure the continuity of their operations even in the face of cyber incidents. Regular data backups and reliable recovery systems are crucial for minimizing downtime and quickly restoring operational technologies. Additionally, introducing redundancy measures, such as redundant components and alternative pathways, ensures that critical systems can continue functioning even if certain components or systems are compromised. By prioritizing resilience and redundancy, organizations can enhance their ability to withstand and recover from cyber threats, maintaining the uninterrupted operation of their critical infrastructure.
In the realm of critical infrastructure, strengthening resilience and redundancy is paramount for mitigating the impact of cyber threats on operational technologies. Implementing robust backup and recovery systems is essential to safeguard valuable data and ensure a quick restoration of services in the event of a cyber incident. Regular data backups help prevent data loss and enable organizations to recover critical information efficiently. Furthermore, introducing redundancy measures adds an additional layer of protection by incorporating duplicate components and alternative pathways. This ensures that even if a component or system fails or is compromised, there are alternative resources available to maintain uninterrupted operations. By strengthening resilience and redundancy, organizations can minimize the potential impact of cyber threats on their operational technologies, improving the overall security and reliability of critical infrastructure.
Continuous Monitoring and Improvement

Continuous monitoring and improvement are crucial elements in safeguarding operational technologies within critical infrastructure. By implementing robust monitoring systems, organizations can detect and respond to emerging threats in real-time, reducing the risk of cyber incidents going undetected. Real-time threat monitoring allows security teams to proactively identify and mitigate potential vulnerabilities and breaches. Concurrently, conducting regular security audits and assessments helps identify weaknesses and vulnerabilities within the operational technologies, enabling organizations to implement necessary improvements and enhancements. By adopting a continuous monitoring and improvement approach, organizations can maintain a proactive stance against cyber threats and ensure the ongoing security of their critical infrastructure.
In the dynamic landscape of cybersecurity, continuous monitoring and improvement play a vital role in safeguarding operational technologies within critical infrastructure. By implementing robust monitoring systems, organizations can stay vigilant and promptly respond to emerging threats. Real-time monitoring enables the detection of suspicious activities, enabling security teams to take immediate action to mitigate potential risks. Additionally, regular security audits and assessments provide valuable insights into the effectiveness of existing security measures and identify areas for improvement. By addressing identified weaknesses and vulnerabilities, organizations can enhance their overall security posture. By adopting a proactive approach of continuous monitoring and improvement, organizations can stay one step ahead of cyber threats, ensuring the ongoing protection of their operational technologies and critical infrastructure.




